cw
AI-Assisted Discharge Summary (AI-Assisted DSUM)
The AI-Assisted Discharge Summary (AI-Assisted DSUM) is a technological innovation aimed at improving the efficiency of hospital discharge summaries within the NHS. Using artificial intelligence (AI) integrated into the NHS Federated Data...
Enhancing NHS Efficiency Through In-Trust Inventory Management Systems (IMS): A Comprehensive Approach to Supply Chain Optimisation and AI Integration
Introduction: The Importance of Inventory Management in NHS Trusts In the ever-evolving landscape of healthcare, managing resources efficiently is critical for delivering high-quality patient care while minimising costs. The National Health Service...
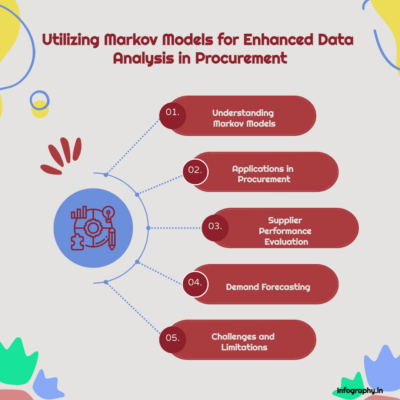
Understanding the Markov Model and Its Use in Data Analysis: Applications in Procurement with PowerBI
The rapid evolution of data analysis and machine learning in modern industries has given rise to advanced methods of interpreting, forecasting, and optimizing processes. Among the various analytical tools available, the Markov...
Improving Accountability in UK Government Procurement: A Comprehensive Review
This article analyses the key findings from the Institute for Government report titled Improving Accountability in Government Procurement, which explores the size and structure of UK government procurement, the challenges of accountability,...
Creating Business Insights from Data: Moving Beyond Dashboards with Power BI
In today’s data-driven business landscape, organisations are flooded with more data than ever before. From transaction histories to customer behaviour patterns, data can drive decision-making at all levels. However, the mere collection...
Risk Stratification: A Tool Falling Short in Real-World Impact
Risk stratification has long been heralded as a promising approach in healthcare, aiming to identify patients at varying levels of risk for adverse health outcomes. The fundamental idea is that by accurately...
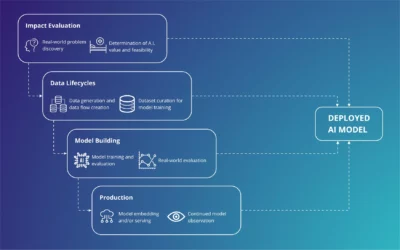
Streamlining AI Development: A Vertically Integrated Approach for Seamless Model Deployment
Vertically integrated artificial intelligence (AI) development model, which breaks down the traditional barriers between different supply chain components, aiming for a more streamlined and cohesive approach. The model is structured in layers,...
Overcoming Challenges in NHS Procurement with Data-Driven Strategies
NHS procurement is fraught with challenges ranging from complex regulatory frameworks and budget constraints to supply chain disruptions and technological limitations. The introduction of the new Procurement Act 2023 adds another layer...